Thursday, 1 August 2024
Digital Signature Algorithm: explanation with block diagram.
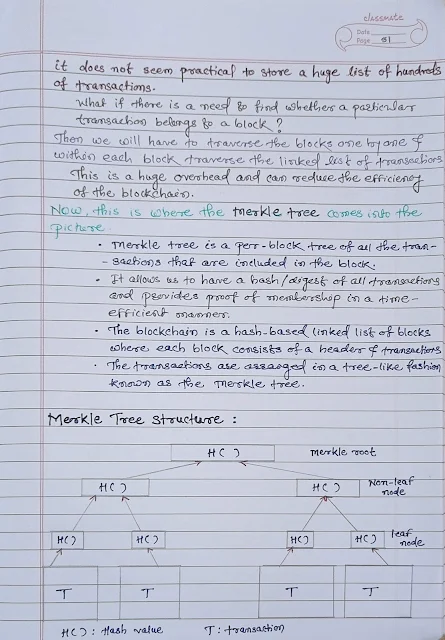
Digital Signature Algorithm:
As we know, DSA use public key cryptography that is Asymmetric key cryptography algorithm for encryption.
1. So, both sender and receiver generate the public key and private key.
2. To generate digital signature.
2.1 Take a plain text pass it to SHA256 hash function it will generate digest of 256 bit.
2.2 When we combine this 256-bit digest with private key of sender we will get a digital signature.
2.3 Take a plain text encrypt it with receiver's public key we will get encrypted message.
3. Once we will get digital signature and encrypted message from sender side then send it to the network
on receiver side.
4. on receiver side we have to unlock this with the help of receiver public key.
4.1 Encrypted message we have to decrypt with the help of private key of receiver.
4.2 We will get a plain text, send that plain text once again to the SHA-256 hash function.
4.3 We will get digest d2 from this of 256 bits.
4.4 After unlocking with the public key of receiver we will get two things encrypted message and
digest d1.
4.5 Compare digest d1 with digest d2 if both finds equal that means we will receive untampered or
original message as it is. if digest d1 is not equal to digest d2 that means we are not getting
original message.
How does SHA256 algorithm works?
How does SHA- 256 algorithm works?
A Step by step detailed explanation of SHA-256 algorithm with example.
Step 1: Pre Processing:
Exercise for you:
How many bits you will pad for input message length of 2348 bits?
Solution:
Step 2: Initialize Hash Values (a, b, c, d, e, f)
Step 3: Initialize round constants K. (K0.. K63)
Step 4: Chunk Loop (0 .. 63)
Tuesday, 30 July 2024
Explain elliptic curve cryptography algorithm in detail with example step by step ?
Elliptic Curve Cryptography Algorithm : in detail with example step by step explanation is as follows.
Monday, 29 July 2024
What is Elliptic Curve Cryptography? Part 1 Basics Knowledge required about Elliptic Curve in detail with 10 Questions
What is Elliptic Curve Cryptography?
Part 1: Basics Knowledge required about Elliptic Curve in detail with 10 questions.
Before studying the Elliptic Curve Cryptography We must have knowledge of following Basic Things:
Those are as follows:
1. What is an Elliptic Curve?
2. What Kind of x and y values are going to be used to form Elliptic Curve?
3. Which type of curve is going to be used in Elliptic Curve Cryptography?
4. What is finite field?
5. How to construct Elliptic Curve over a Finite Field Z/11?
6. What are the Characteristics of Elliptic Curve?
7. How to Compute addition of Two different points P and Q on elliptic curve i:e P + Q = R ?
7. How to Compute addition of same points P with P on elliptic curve i:e P+P = 2P ?
Subscribe to:
Comments (Atom)






.jpg)







































.jpg)



