Tuesday, 20 August 2024
Thursday, 8 August 2024
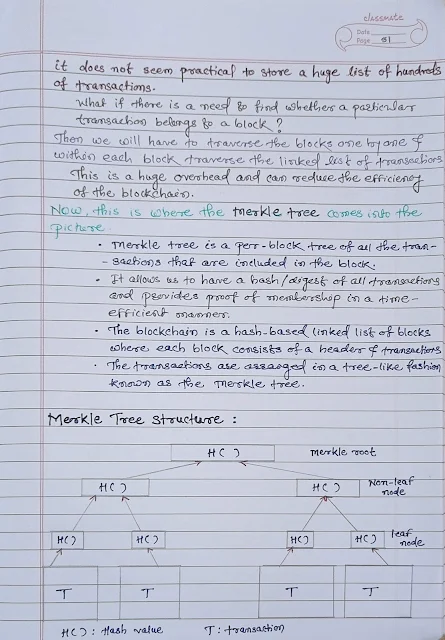
Friday, 2 August 2024
Thursday, 1 August 2024
Digital Signature Algorithm: explanation with block diagram.
Digital Signature Algorithm:
As we know, DSA use public key cryptography that is Asymmetric key cryptography algorithm for encryption.
1. So, both sender and receiver generate the public key and private key.
2. To generate digital signature.
2.1 Take a plain text pass it to SHA256 hash function it will generate digest of 256 bit.
2.2 When we combine this 256-bit digest with private key of sender we will get a digital signature.
2.3 Take a plain text encrypt it with receiver's public key we will get encrypted message.
3. Once we will get digital signature and encrypted message from sender side then send it to the network
on receiver side.
4. on receiver side we have to unlock this with the help of receiver public key.
4.1 Encrypted message we have to decrypt with the help of private key of receiver.
4.2 We will get a plain text, send that plain text once again to the SHA-256 hash function.
4.3 We will get digest d2 from this of 256 bits.
4.4 After unlocking with the public key of receiver we will get two things encrypted message and
digest d1.
4.5 Compare digest d1 with digest d2 if both finds equal that means we will receive untampered or
original message as it is. if digest d1 is not equal to digest d2 that means we are not getting
original message.
Subscribe to:
Comments (Atom)

















































.jpg)